
Implanted medical devices present different security issues than traditional information systems, and require different security risk analysis and mitigation techniques.
Over the past fifty years implanted medical devices have undergone at least four major, technology-driven paradigm shifts—major changes in world-view for designers, users, and recipients of such devices.
The first was the miniaturisation of electronics and batteries that allowed devices to be implanted entirely within the body. The second was the addition of flexibility with multiple device configuration parameters settable by an external “programmer”. The third was the replacement of hard-wired control circuitry with programmable microprocessors, making implanted devices much more flexible, powerful and sophisticated. The fourth is upon us: it is the introduction of “real-time” autonomic networking of implanted devices, allowing them to communicate with other medical devices at a distance, and “at will”, without any action on the part of the patient.
It is the operational and design consequences of this fourth paradigm shift that we will discuss here. Our focus will be on the implications of the networking of implanted medical devices (IMDs) for device and patient data.
Our model will be IMDs for cardiac-rhythm therapy—pacemakers, cardioverter-defibrillators, resynchronisation devices, etc.
Paradigm shift from standalone to networked IMDs
Until 2000, IMDs were mostly isolated, standalone, electronic devices, communicating infrequently with external devices, and then only by near proximity (5cm to 10cm) inductive telemetry. Some of these IMDs can emit sounds to alert the patient to an abnormal condition, but all other external communication requires that the IMD be “interrogated” by an external device (a programmer) under human control. External device telemetry allows a caregiver, in a clinical setting, to modify IMD therapy parameters, check the IMD status and retrieve stored device and physiological data.
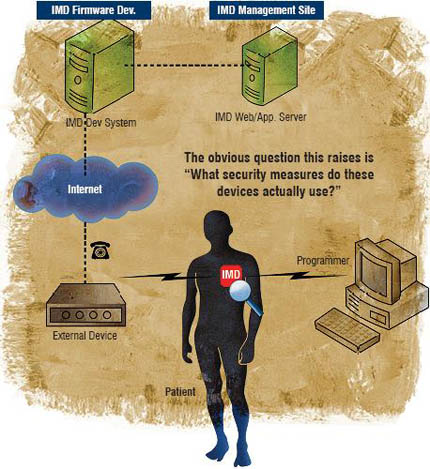 The newest families of IMDs are microprocessor controlled and, most important for our discussion, equipped with radio-frequency (RF) transceivers allowing them to communicate with distant (2m to 20m) external devices, and to do so autonomously. We refer to these IMDs capable of distant RF telemetry as “Networked” IMDs or NIMDs. The newest types of external devices may be clinical programmers in the traditional sense, or “read-only” home monitoring devices. They may also be in-home monitors with limited IMD programming capabilities.
The newest families of IMDs are microprocessor controlled and, most important for our discussion, equipped with radio-frequency (RF) transceivers allowing them to communicate with distant (2m to 20m) external devices, and to do so autonomously. We refer to these IMDs capable of distant RF telemetry as “Networked” IMDs or NIMDs. The newest types of external devices may be clinical programmers in the traditional sense, or “read-only” home monitoring devices. They may also be in-home monitors with limited IMD programming capabilities.
NIMD products, related services and the system view
The latest generation of (cardiac-related) NIMDs, all of which use RF telemetry to network with external devices, include devices from Biotronik, Guidant and Medtronic (introduced in 2000, 2005 and 2006 respectively).
Remote (usually in-home) monitoring enabled by NIMDs is growing, as demonstrated by the rapid deployment and growth of such systems as Biotronik’s Home Monitoring, Medtronic’s CareLink® Network, St. Jude Medical’s Housecall Plus™ and Guidant’s LATITUDE® Patient Management System (introduced in 2000, 2002, 2003 and 2005 respectively).
These new NIMD products and related services lead us to take a much broader view of the networked IMD as part of a large, distributed information system, as illustrated below. Therefore, the obvious question this raises is: “What security measures do these devices actually use?”
Information security consequences of NIMDs
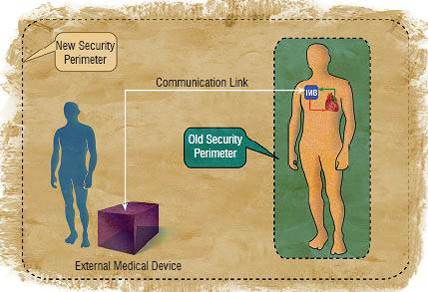
A critical security consequence of the isolation of IMDs within their patient’s bodies is that the effective boundary for security concerns, or the “security perimeter” is an imaginary envelope about 10cm outside the patient’s body. A critical consequence of networking IMDs to external devices is that the effective boundary for security concerns, the security perimeter, is greatly expanded. These old and new security perimeters are illustrated in the figure below.
This should make it clear why, in the past, access to sensitive IMD information required either very close proximity (essentially, physical access) to the IMD or access to printed reports or charts. Data availability only required the patient and a suitable programmer, and data confidentiality and integrity were assured by operational procedures characteristic of good clinical practice.
Today, with the introduction of RF telemetry for device interrogation and programming, access to sensitive IMD data becomes much harder to control. Data availability, confidentiality and integrity depend upon the security of the RF data link, the ability of the IMD itself to verify the suitability of an RF external device, and the ability of the RF external device to verify that it is communicating with the right IMD. The staging of device data and programming commands in external, networked devices also raises access control issues, depending upon the location and physical control of the external devices.
The result of these differences is a significant increase in the risk of data confidentiality, integrity or availability compromise; this is precisely the definition of information security risk. This increase in information security risk makes information security management a much larger concern for new NIMDs because, as discussed above, their sensitive data are transmitted over an open channel (RF) and stored in (relatively) uncontrolled external medical devices. There are three drivers for this heightened concern with information security:
Addressing the NIMD information security risk
Medical device manufacturers and the caregivers (who prescribe and manage medical devices) need to understand that the clinical benefits of networking IMDs (with external systems) bring with them not only new benefits:
 These benefits are accompanied, however, by new responsibilities placed mostly on device manufacturers. Foremost of these is the responsibility to understand and manage the information security risks introduced by such networking. These information security risks could be described as (broadly speaking):
These benefits are accompanied, however, by new responsibilities placed mostly on device manufacturers. Foremost of these is the responsibility to understand and manage the information security risks introduced by such networking. These information security risks could be described as (broadly speaking):
Fortunately, information security risk management is an established discipline, with methods and processes that are easily adapted to the world of IMDs.
Such an analysis will identify the high-level information security requirements for NIMDs and external devices, as well as any centralised medical information servers they communicate with. By identifying and implementing technical mitigations, device manufacturers can eliminate or significantly reduce these information security risks.
Security relevant steps in medical device development process
All of the above risks need to be considered in the light of a thoughtful information security risk assessment
These security relevant steps are very much like the safety relevant steps in the classic IMD development process. As with Safety Risk, information Security Risk needs to be considered early in the process.
Suggestions for NIMD developers (from the trenches)
Based upon my own professional experience, and upon research into the experience of others, in the management of security in NIMD-based systems, I have derived the following observations:
This leads to my gentle suggestion that early consideration of privacy and security issues in the device development process is essential to contain the cost and limit the schedule impact of implementing of security requirements.
While the terminology or information security is probably new and somewhat foreign to many IMD developers, there are useful parallels with safety and hazard analysis. There is also a rich source of knowledge on information security risk management in the information security literature, on the World Wide Web, in books and in magazines and journals.
Conclusions
In conclusion, we see that networking implanted medical devices introduces a new type of risk—information security risk—that can have both safety and legal consequences. Even as a clearly beneficial technology advance, medical device networking must pass a marketplace acceptance test; that is, its benefits must be acceptable to its users, patients and caregivers. Patients and caregivers are more aware of, and concerned with, risks to safety and to privacy, than at any time in the past. Addressing information security risk is, thus, essential to marketplace acceptance of networked medical devices.
This is why information security risk assessment and mitigation are becoming part of the networked medical device development and approval processes. Much like Safety Hazard Analysis, Information Security Risk Analysis is most effective when performed early in the device development process. In this new medical device paradigm, patient and caregiver acceptance of information security risks follows from the same type of assurances as their acceptance of safety risk.