

Consumers worldwide are concerned about security. In fact, it would be more appropriate to say that they are consumed with fear and anxiety about it. The 2017 Unisys Security Index – the only recurring snapshot of security concerns conducted globally – stands at 173 out of a possible score of 300. This is a troubling 20 percent higher than results were in 2014, and is the highest score since the survey’s inception ten years ago. Identity theft and bankcard fraud top the list of consumer concerns.
These concerns are very justified when applied to healthcare. In 2017, healthcare had the unfortunate distinction of suffering the greatest number of breaches compared to all other industries (27 percent of all breaches), comprised of 471 publicly-disclosed incidents.1 For example, in Australia, 63 organisations have experienced data breaches since February 22, 2018, with 24 percent of those data breaches occurring in healthcare.2
There is no relief in sight. IDC Health Insights predicts that the situation surrounding ransomware will get worse before it gets better, with the incidence of ransomware doubling in 2018 compared to 2016 as cybercriminals get more brazen and their attacks get more sophisticated. The impact of a successful ransomware attack is that mission-critical clinical systems are not available when IT systems are taken offline for remediation, creating patient safety issues and resulting in lost revenue opportunities when patients are diverted to other institutions.3
Why are healthcare organisations being targeted by hackers? There are two primary reasons. First, healthcare is a laggard industry from a technology adoption standpoint. Consequently, the robust security stance that is present in other industries is lacking in healthcare. Gaps and vulnerabilities abound – and hackers are swift to take advantage of them.
Second, there is a great deal of latency in healthcare processes. Healthcare billing systems are often fragmented with no single bill, and billing is often not complete for up to a month post-discharge. Therefore, if a hacker steals that person’s data, a month or more can go by before anyone even realises that the data has been stolen. During that month, the hacker can use the data at will to build an independent persona and make financial transactions and purchases. In contrast, when a credit card is stolen, the breach can be identified and the account shut down within a short period of time – sometimes within minutes.
Laggard technology and high latency combine to form a hacker’s dream – and a hospital’s nightmare.
One of the easy-to-access vulnerabilities that hackers can target in healthcare IT networks is medical devices. This risk arises from the use of integrated omputational devices that host the medical device control programming, and from the use of network connectivity to communicate data. Medical devices have become computing devices and, when deployed on open networks within the healthcare provider enterprise, they are vulnerable to the same cybersecurity risks as most other IT resources inside the organisation.4
Medical devices have been used as entry points for several highly-publicised cybersecurity events recently. For example, in 2016, Johnson & Johnson warned over 100,000 patients who were using its Animas OneTouch Ping insulin pump that a hacker could exploit a vulnerability to overdose diabetic patients with insulin. The Animas OneTouch Ping was sold with a wireless remote control that patients can use to order the pump to dose insulin.5 Then, in 2017, medical devices were hit by WannaCry ransomware. Two Bayer Medrad devices, which provide imaging improvements for MRIs, were infected.6
Adding to the medical device security challenge, the healthcare industry is in the process of rolling out remote patient monitoring solutions. These devices give caregivers of homebound patients who are reliant on pulse oximeters, respirators, and the like the ability to not have to sit by the bedside, but rather be notified by smart phone of alerts or of changes that might lead to alerts. These devices have to be connected to function. Without proper security, they are even more vulnerable than devices in the hospital, often without the benefit of even rudimentary firewalls.
The fact is, the security perimeter for healthcare is constantly changing. Organisations are harnessing the functionality of the cloud for data and processes while, concurrently, there is an increase in the use of wearables, sensors, and tablets for communication and data retrieval. There is an insatiable need for contextually-appropriate information. CIOs are therefore tasked with protecting assets inside the traditional security perimeter as well as new assets external to the traditional security perimeter to establish a multi-level adaptive defense mesh surrounding the virtual enterprise.
Gartner notes that healthcare provider CIOs should protect their patients and their organisations by understanding the specific vulnerabilities associated with medical devices and create the necessary strategies and action plans to minimise the risk.7
Given the serious concerns that exist regarding the security of medical devices, how are hospitals and healthcare systems dealing with the matter? At Unisys, we partnered with HIMSS Media to conduct a survey in March 2018 to better understand how healthcare providers/practices are managing their medical devices.8 The survey reported that more than 8 out of 10 providers consider medical device security a strategic priority, but just over one-third of providers have approved budgets.
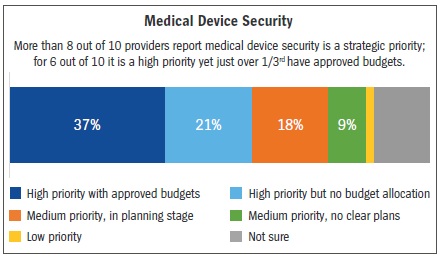
The lack of approved budgets is troubling. There have been at least eight SamSam ransomware attacks on healthcare and government organisations since the beginning of 20189 as of the writing of this paper. There is no time to be lost: security must be a priority for all healthcare practices, with solid budgets and aggressive plans to turn that priority into a reality.
Digging deeper, the survey revealed what types of medical device security protocols hospitals and healthcare practices currently have in place.
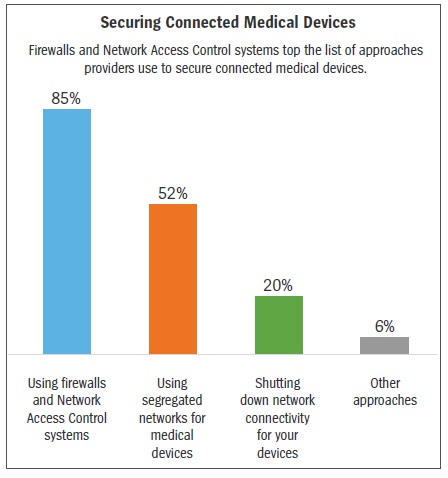
In the survey, 85% of respondents stated that they use a combination of firewalls, virtual private networks (VPNs), and network access control (NAC) systems. Firewalls and NACs are, indeed, great for stationary security. However, many medical devices are mobile. They move (often on a daily basis) around the healthcare facility. While firewalls and NACs can be manipulated to allow for devices that are mobile, this protection is difficult to establish and maintain. Plus, without encryption, security gaps remain for hackers to probe.
The second highest response indicated that 52% of practices use segregated networks for their medical devices. Another 20% simply shut down network connectivity for their devices. While healthcare organisations may believe that these options provide network security, in reality, they do not. Plus, they inhibit the vital real-time flow of data from medical devices to hospital systems and electronic medical records (EMRs). Segregation or shut-down may require patient data to be entered into EMRs manually, which causes a delay and can compromise data accuracy.
Regulatory organisations worldwide are taking increasing notice of the need to secure medical devices. In the US, the Food & Drug Administration (FDA) has stated that “medical device manufacturers and healthcare facilities should take steps to ensure appropriate safeguards. Manufacturers are responsible for remaining vigilant about identifying risks and hazards associated with their medical devices, including risks related to cybersecurity. They are responsible for putting appropriate mitigations in place to address patient safety risks and ensure proper device performance. Hospitals and healthcare facilities should evaluate their network security and protect their hospital systems.”10
In Australia, the regulation of pharmaceuticals and medical devices is managed by the Therapeutic Goods Administration (TGA), which is an arm of the Australian Government Department of Health. While the TGA manages operational safety and effectiveness of medical devices, there is room for improvement. All fixed, mobile, and implantable medical devices need to be safeguarded from malicious access. Patients’ reliance on these devices means that safety cannot be compromised.
Gartner predicts that, by 2020, the number of medical devices requiring security hardening by a healthcare provider will increase by 45% and more than 25% of identified attacks in healthcare delivery organisations will involve the Internet of Things (IoT).11 Given these sobering figures, what steps should healthcare organisations take?
Forrester recommends six strategic actions12:
1. Require multifactor authentication for all sensitive systems
2. Quantify the sensitivity of all assets
3. Define a strategy to handle all data based on its sensitivity
4. Segment and secure the network
5. Embed internal and external regulatory compliance protocols
6. Encrypt all sensitive data
Achieving such security may seem a daunting task, but it is not. A medical device management system that incorporates microsegmentation and data encryption addresses security issues by supporting and enhancing the security inherent within each medical device (whether wearable or on-site), and by protecting connected devices that lack any security features of their own. Such a system allows the creation of communities of interest within the hospital or healthcare organisation so that only the people who need to see data from a device can access that data. For example, a clinician may only be able to see data generated by a patient monitor, whereas a biomedical engineer may have a view into data about the device itself. Other personnel – and, most importantly, hackers – would be unable to gain any visibility into the device or its data. As hospitals and healthcare organisations implement such robust security, they will be able to maintain consumer trust by proving that personal data is safe and secure, wherever it resides.
Unisys is a leader in providing zero-trust security built on identity-based microsegmentation. We work with healthcare providers to help them to meet the needs of today’s information and medical device security crisis. Your organisation’s ability to protect sensitive and private information and critical medical devices is core to maintaining reputation. The tools, approach, and expertise we provide can help you plan, protect, and prepare for the future of your hospital or healthcare organisation. To help you get started, Unisys offers a complimentary dark market data scanning service to assess your organisation’s risk status. For more information, Please visit www.unisys.com or email me bou.lai@unisys.com to find solutions that suit you best.
References:
1 “2017 Data Breach Level Index,” Gemalto.
2 Minion, Lynne. “Healthcare suffers almost a quarter of data breaches, as reports skyrocket under mandatory notification scheme,” Healthcare IT News, April 11, 2018.
3 IDC FutureScape: Worldwide Healthcare IT 2017 Predictions.
4 Exposing the Security Risks of Medical Devices, Gartner 2018.
5 Finkle, Jim. “J&J warns diabetic patients: Insulin pump vulnerable to hacking.” Reuters, October 4, 2016.
6 Seals, Tara. “#WannaCry hits medical devices in the US.” Infosecurity Group, May 18, 2017.
7 Exposing the Security Risks of Medical Devices, Gartner 2018.
8 A total of 101 qualified respondents completed the survey, with nine out of ten respondents being employed by hospitals, AMCs, and IDNs, and the balance coming from ambulatory or other ancillary healthcare practices.
9 Cohen, Jessica Kim. “HHS issues new guidance on SamSam ransomware.” Becker’s Health IT and CIO Report, April 10, 2018.
10 https://www.fda.gov/MedicalDevices/DigitalHealth/ucm373213.htm
11 Healthcare Provider CIOs Need to Address IoT’s Security Risks Now, Gartner, January 2017.
12 Healthcare Must Embrace Zero Trust To Address PHI Vulnerabilities, Forrester, March 2017.