
There is lots of noise around the FBI report warning companies about attacks that bypass MFA. Our own research shows MFA solutions are not being widely adopted and most likely because they are thought to prove complex and time-consuming to manage. We explain why MFA should definitely be turned on in Healthcare organisations and 6 points to remember for a successful MFA deployment.
The healthcare industry is a prime target for hackers. In all countries, private and public organisations hold sensitive information about millions of individual patients. This includes personal data such as your date of birth and address, your social security number, billing information and, of course, medical records – all of which can be used for a large number of fraudulent actions. Identity-theft and data privacy expert Carrie Kerskie concludes “Medical identity theft is the deadliest form of identity theft”.
In recent years, institutions have struggled to defend their network perimeter and keep cybercriminals at bay. The thing is, credentials are easily compromised and this constitutes one of the most dangerous risks to a healthcare organisation. But detecting those attacks is a real challenge. Once the attacker is able to steal a set of credentials, they are then in possession of valid credentials. From then, no security solution will detect anything suspicious because they consider that the person logging in is who they say they are.
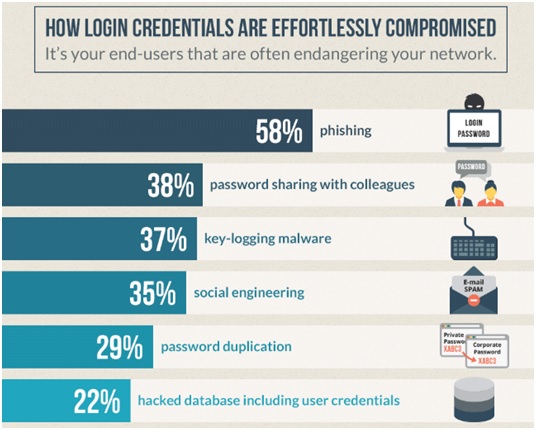
IS Decisions' research into the access security priorities of 500 IT Security Managers in the US and UK
It’s easy to blame your employees. But employees are human. They are flawed, careless and often exploited. Security must be there to protect employees from both careless and malicious behaviour and to protect the organisation from outsiders trying to gain access by pretending to be employees.
This is where we need multi-factor authentication (MFA). It represents one of the most secure controls to stop unwanted access. Without it, hackers can easily bypass all of the other security measures. But sadly, even though healthcare organisations know the risk, many still don’t take password security seriously. What’s holding them back?
Healthcare organisations have the wrong idea about MFA
1. MFA is for organisations of any size
You might think “my organisation is too small to use MFA”. Well you’re wrong. The data you want to protect is as important as any other big healthcare organisation. Every healthcare institution, no matter the size, should use MFA to protect their accounts. MFA is not necessarily difficult, costly or frustrating.
2. MFA should be used to protect every user
You also may think “I don’t need MFA because I don’t have any privileged users”. Wrong again. Especially in healthcare organisations, MFA should be used to protect every user within your organisation. Your users have access to enough data that, if used inappropriately, could harm your organisation. Take a nurse as an example, what happens if she sells a celebrity patient’s data to a newspaper?
The second reason you should protect every user is that most attackers won’t start with a privileged account. Usually, they want to start with an “easy” target. Once they have access to the network, they then move laterally to find anything valuable.
3. MFA isn’t perfect
“Perfect” is a word that doesn’t exist in IT security. However, MFA is quite close. A few weeks ago, the FBI highlighted some recent attacks where MFA had been bypassed. Two main authenticator vulnerabilities were found: ‘Channel Jacking’, involving taking over the communication channel that is used for the authenticator and ‘Real-Time Phishing’, using a machine-in-the-middle that intercepts and replays authentication messages. Specialists agree to say that these attacks require a lot of money and efforts. Usually, cyber criminals who come across MFA will rather change target to find an easier one.
Despite those attacks, the FBI still thinks MFA is very effective.
4. MFA doesn’t mean disruption
In healthcare organisations, disruption is a challenge. When it comes to implementing a new solution, it needs to be smooth, fast and not disrupting. This is why flexibility and customisation are needed with MFA. What you can do is use MFA togetherwith contextual controls to improve identity assurance. In other terms, you use environment information to further confirm all users’ identity without disrupting productivity.
Without MFA, the healthcare industry is wide open to attack. It should be a key security measure for any healthcare organisation, and can be one of the easiest ways to keep breaches away.