In this interview, we explore why cloud computing has taken root and list some advantages for health providers willing to pursue this as major IT transformation. We also discuss cloud variants or types, point out cultural barriers for adoption, and concerns when securing health information in the cloud.
1. What is Cloud computing and how does it benefit healthcare providers and consumers?
Three fundamental things have spawned the surge of interest in cloud computing
Combined these three aspects provide a flexible pool of computing, network and storage resources, which loosely defined is the ‘cloud’. Diving deeper, or for a more precise explanation of the cloud and its subsequent benefits to healthcare providers and consumers, we find that the ‘Cloud’ offers:
 On-demand self-service A consumer can unilaterally provision computing capabilities such as server time and network storage as needed automatically, without requiring human interaction with a service provider.
On-demand self-service A consumer can unilaterally provision computing capabilities such as server time and network storage as needed automatically, without requiring human interaction with a service provider.
Resource pooling The provider’s computing resources are pooled to serve multiple consumers using a multi-tenant model. Different physical and virtual resources are dynamically assigned and reassigned according to consumer demand.
Rapid elasticity Capabilities can be rapidly and elastically provisioned —. To a Healthcare provider the capabilities available for provisioning often appear to be unlimited and can be purchased in any quantity at any time.
Measured service Resource usage can be monitored, controlled, and reported — providing transparency for both the provider and consumer of the service.
Thus there are lots of possible uses of the cloud in can substantially improve healthcare delivery and make it cheaper to implement. Some clear examples include:
Innovative imaging PAC systemswhere several hospitals could share a single expensive Pictorial Archiving and Communications (PACS) or Radiology imaging system. One hospital would manage the PACS and simply charge an administrative fee. Not only would it lower costs for all hospitals but teleradiology specialists all over the world can now easily share diagnostic images to examine difficult cases.
Innovative Electronic Medical Record (EMR) delivery and exchange. Rather than upgrading software on a regular basis as one would with regular EMR systems, a cloud based EMR service and allows hospitals with a simple way to keep their systems updated. So one can get the benefit of advanced technology without having to invest in a large IT staff.
Data mining of healthcare case studies allows for better etiology, disease management and more effective therapies. But data mining is usually an expensive proposition for a single small hospital accomplish on its own. By aggregating data mining into a ‘shared resource’ through the cloud many more hospitals can now afford the full benefits of data mining.
In short, the sky is the limit to the way the cloud can be used for the Cloud has the potential to makes healthcare IT much cheaper, faster, better.
2. What are the major concerns of securing health information in the cloud?
Perhaps the question could be broadened to ask if the cloud is more secure. The clear answer to this is that Cloud Computing isn’t necessarily more or less secure than your current environment. In some cases moving to the cloud provides an opportunity to re-architect older applications and infrastructure to meet or exceed modern security requirements. At other times the risk of moving sensitive data and applications to an emerging infrastructure might exceed your tolerance.
However cloud security has the vast potential to surpass the levels of information security that are possible today but only if it is done right. This begs the question, how is Cloud security different from traditional IT security?
Let’s consider a traditional (or non cloud) data center’s security requirements and approach. Again, that is something that is not in cloud mode. Several things occur to ensure security in a traditional data center:
But in the cloud everything changes…. As physical visibility is lost …. With the cloud, unlike a traditional data center, our concerns or questions arise:
3. What factors need to be considered while adopting a cloud-based solution?
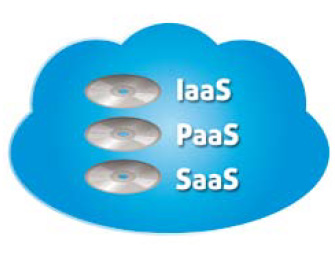
We can make three different types of clouds based on the required service model:
Differences among these three types of clouds are vitally important because they carry important ramifications for a wide range of operating and security requirements.
Infrastructure as a service (IaaS) includes the infrastructure resource stack from the facilities to the hardware platforms that reside in them and the logical connectivity to those resources. So IaaS provides few if any application-like features, but enormous extensibility. So for healthcare provider this generally means less integrated security capabilities and functionality beyond protecting the infrastructure itself. In short, this model requires that operating systems, applications, and content must be managed and secured by you the healthcare provider.
Platform as a service (PaaS) sits atop IaaS and adds an additional layer of integration by providing application development frameworks and middleware capabilities. These added functions include database and message queuing. PaaS is primarily used to enable in-house developers to build their own applications on top of the platform. However built in security capabilities are still not fully complete because of this flexibility. So when using this model the hospital still assumes considerable risk but the risk is less than a pure IaaS model.
The final cloud variant is software as a service (SaaS). SaaS, in turn, is built upon the underlying IaaS and PaaS stacks. It provides a self-contained operating environment used to deliver the entire user experience including the content, its presentation, the application(s), and management capabilities. So SaaS provides the most integrated functionality built directly into the offering, but it has the least the least consumer (hospital) extensibility. And because of this, a SaaS provider must guarantee a relatively high level of integrated security. The SaaS cloud provider in essence bears a responsibility for most of your information security.
The key takeaway for security architecture is that the lower down the stack the cloud service provider stops, the more security capabilities you, as the cloud consumers, are responsible for implementation and management
4. Do you think healthcare sector is better positioned to adopt cloud than others?
Actually every industry can be a beneficiary of the cloud. But Healthcare, which is often cost constrained and is more about doing societal good than profit, should be very receptive to its adoption.
5. How has the industry's initial experience with the cloud been?
There are clear opportunities and options for healthcare providers. The initial forays have been with Electronic Medical Records, and point solutions say for revenue cycle applications. Over time we expect many more applications to flourish.
6. Are there any cultural issues that could hinder the adoption of cloud?
First and foremost, the cloud presents those of us in information technology and security a once-in-a career opportunity to make information security better: faster, cheaper, more efficient and less intrusive. Because cloud platforms are still developing, we have unprecedented opportunities to embed information security processes and technologies deeper into the infrastructure. This requires a deep change in the cultural mindset of organisations used to a strong centralised IT function.
More critically your business units must also be ready to share the same infrastructure. For a cloud solution to make economic sense it has to have periods of high utilisation; otherwise, the resources will sit idle for long periods of time, destroying the return on investment.
7. There exist health information security and privacy concerns in the cloud; How can these issues be recognised?
 The cloud forces user organisations to fully reexamine their methods for Data ownership and control. Therefore we may to revise our models for establishing trust and consequences and chain of custody, and how we provide access and authentication.
The cloud forces user organisations to fully reexamine their methods for Data ownership and control. Therefore we may to revise our models for establishing trust and consequences and chain of custody, and how we provide access and authentication.
Providers of Cloud services must also have give user administrators (hospitals) the access and privileges needed to do their jobs. That is user organisations should clearly retain control over IT policies and assets, even if they don’t own or directly operate those assets.
One other important point: in the cloud Interactions between software and systems often equal or exceed those between people and machines. Consequently, it’s imperative for IT and security processes to account for the reality that a ‘user’ in the cloud may more likely be a machine than a person (or a machine acting on behalf of a person). This has profound implications on how identities are provisioned, authenticated and managed
8. What are the key steps to overcome/manage these issues?
In short, the best way to ensure security and privacy for the cloud is for enterprise customers to require maximum transparency into their cloud providers’ operations. You will be sharing resources with potentially lots of business units – external or internal – and you need to know what is going on
Also as a CIO or Chief Security Officer you must change your mind-set about information security. Several things are important:
9. Any other comments?
There are many other cloud related issues that will affect users, IT managers and senior management. Consider one aspect, that of compliance. Many IT professional have to constantly worry about audits. Moving to the cloud means you will likely be inundated by audit such as systems reviews, transaction reviews, policy and procedure reviews and risk assessments. This is a heavy information dissemination, storage and analysis burden. It happens that information security is tied closely to information movement and will be among first compliance items we design for the cloud. So if we do this correctly for information security efforts, we can substantially improve other compliance needs in healthcare.